Page 14 - Security testing for USSD and STK based Digital Financial Services applications Security, Infrastructure and Trust Working Group
P. 14
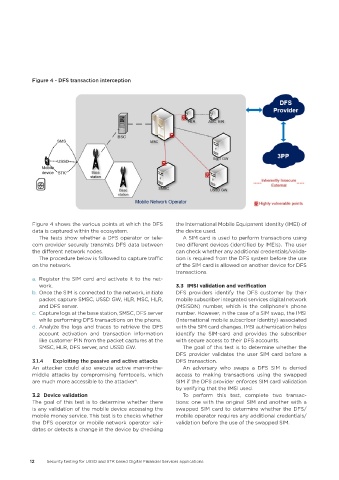
Figure 4 - DFS transaction interception
Figure 4 shows the various points at which the DFS the International Mobile Equipment Identity (IMEI) of
data is captured within the ecosystem. the device used.
The tests show whether a DFS operator or tele- A SIM card is used to perform transactions using
com provider securely transmits DFS data between two different devices (identified by IMEIs). The user
the different network nodes. can check whether any additional credentials/valida-
The procedure below is followed to capture traffic tion is required from the DFS system before the use
on the network. of the SIM card is allowed on another device for DFS
transactions.
a. Register the SIM card and activate it to the net-
work. 3�3 IMSI validation and verification
b. Once the SIM is connected to the network, initiate DFS providers identify the DFS customer by their
packet capture SMSC, USSD GW, HLR, MSC, HLR, mobile subscriber integrated services digital network
and DFS server. (MSISDN) number, which is the cellphone's phone
c. Capture logs at the base station, SMSC, DFS server number. However, in the case of a SIM swap, the IMSI
while performing DFS transactions on the phone. (International mobile subscriber identity) associated
d. Analyze the logs and traces to retrieve the DFS with the SIM card changes. IMSI authentication helps
account activation and transaction information identify the SIM-card and provides the subscriber
like customer PIN from the packet captures at the with secure access to their DFS accounts.
SMSC, HLR, DFS server, and USSD GW. The goal of this test is to determine whether the
DFS provider validates the user SIM card before a
3.1.4 Exploiting the passive and active attacks DFS transaction.
An attacker could also execute active man-in-the- An adversary who swaps a DFS SIM is denied
middle attacks by compromising femtocells, which access to making transactions using the swapped
are much more accessible to the attacker . SIM if the DFS provider enforces SIM card validation
4
by verifying that the IMSI used.
3�2 Device validation To perform this test, complete two transac-
The goal of this test is to determine whether there tions: one with the original SIM and another with a
is any validation of the mobile device accessing the swapped SIM card to determine whether the DFS/
mobile money service. This test is to checks whether mobile operator requires any additional credentials/
the DFS operator or mobile network operator vali- validation before the use of the swapped SIM.
dates or detects a change in the device by checking
12 Security testing for USSD and STK based Digital Financial Services applications