Page 15 - Security testing for USSD and STK based Digital Financial Services applications Security, Infrastructure and Trust Working Group
P. 15
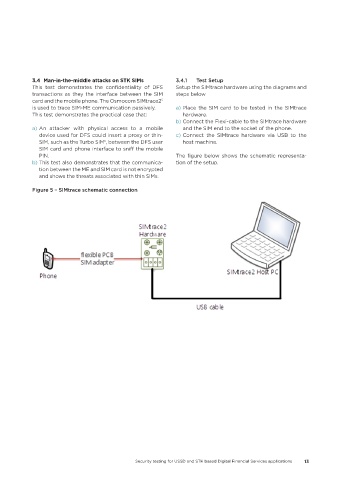
3�4 Man‑in‑the‑middle attacks on STK SIMs 3.4.1 Test Setup
This test demonstrates the confidentiality of DFS Setup the SIMtrace hardware using the diagrams and
transactions as they the interface between the SIM steps below
card and the mobile phone. The Osmocom SIMtrace2
5
is used to trace SIM-ME communication passively. a) Place the SIM card to be tested in the SIMtrace
This test demonstrates the practical case that: hardware.
b) Connect the Flexi-cable to the SIMtrace hardware
a) An attacker with physical access to a mobile and the SIM end to the socket of the phone.
device used for DFS could insert a proxy or thin- c) Connect the SIMtrace hardware via USB to the
SIM, such as the Turbo SIM , between the DFS user host machine.
6
SIM card and phone interface to sniff the mobile
PIN. The figure below shows the schematic representa-
b) This test also demonstrates that the communica- tion of the setup.
tion between the ME and SIM card is not encrypted
and shows the threats associated with thin SIMs.
Figure 5 – SIMtrace schematic connection
Security testing for USSD and STK based Digital Financial Services applications 13