Page 12 - Security testing for USSD and STK based Digital Financial Services applications Security, Infrastructure and Trust Working Group
P. 12
attack or transmitting malicious transactions to trig- b. Capturing traffic at the BTS within the MNO net-
ger a behaviour to the unsuspecting DFS customer. work providers network in the absence of a GSM
The passive and active attacks are described below interceptor
based on the level of access available to the tester. c. Capturing traffic and logs at the MSC, HLR, SMSC
and DFS server
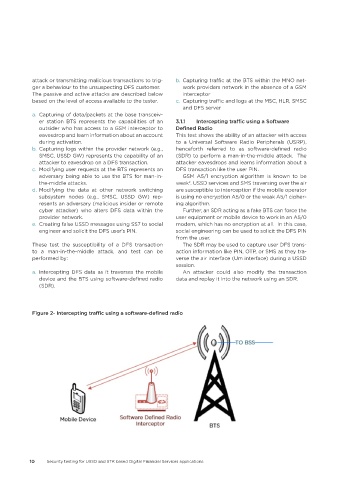
a. Capturing of data/packets at the base transceiv-
er station BTS represents the capabilities of an 3.1.1 Intercepting traffic using a Software
outsider who has access to a GSM interceptor to Defined Radio
eavesdrop and learn information about an account This test shows the ability of an attacker with access
during activation. to a Universal Software Radio Peripherals (USRP),
b. Capturing logs within the provider network (e.g., henceforth referred to as software-defined radio
SMSC, USSD GW) represents the capability of an (SDR) to perform a man-in-the-middle attack. The
attacker to eavesdrop on a DFS transaction. attacker eavesdrops and learns information about a
c. Modifying user requests at the BTS represents an DFS transaction like the user PIN.
adversary being able to use the BTS for man-in- GSM A5/1 encryption algorithm is known to be
the-middle attacks. weak . USSD services and SMS traversing over the air
2
d. Modifying the data at other network switching are susceptible to interception if the mobile operator
subsystem nodes (e.g., SMSC, USSD GW) rep- is using no encryption A5/0 or the weak A5/1 cipher-
resents an adversary (malicious insider or remote ing algorithm.
cyber attacker) who alters DFS data within the Further, an SDR acting as a fake BTS can force the
provider network. user equipment or mobile device to work in an A5/0
e. Creating false USSD messages using SS7 to social modem, which has no encryption at all. In this case,
engineer and solicit the DFS user's PIN. social engineering can be used to solicit the DFS PIN
from the user.
These test the susceptibility of a DFS transaction The SDR may be used to capture user DFS trans-
to a man-in-the-middle attack, and test can be action information like PIN, OTP, or SMS as they tra-
performed by: verse the air interface (Um interface) during a USSD
session.
a. Intercepting DFS data as it traverses the mobile An attacker could also modify the transaction
device and the BTS using software-defined radio data and replay it into the network using an SDR.
(SDR).
Figure 2- Intercepting traffic using a software-defined radio
10 Security testing for USSD and STK based Digital Financial Services applications