Page 11 - Security testing for USSD and STK based Digital Financial Services applications Security, Infrastructure and Trust Working Group
P. 11
Components USSD and STK related threats and vulnerabilities Tests/attack scenarios
Core Network • Inherent SS7 protocol vulnerabilities: Insufficient internal con-
(USSD GW, MSC, trols can allow insider access to customer data. The GSM MAP
SMSC) protocol used for communication between the mobile operator
core nodes transmits in clear text, and this can enable an insider
view PIN and transaction information due to lack of end to end
encryption.
• Information can be spoofed by insiders, particularly in protocols
that provide no notion of message integrity like USSD.
• The increased ease of access to the SS7 network allows an
attacker to use MAP (Mobile Application Part) operations to
insert or modify subscriber data, intercept mobile communica-
tion, or identify subscriber location.
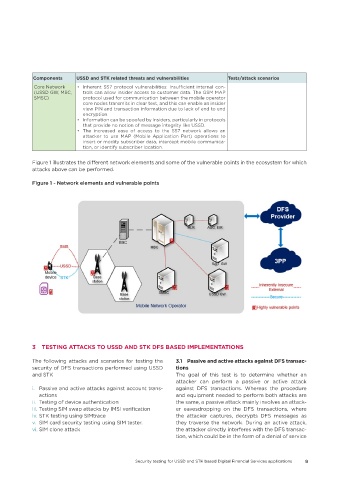
Figure 1 illustrates the different network elements and some of the vulnerable points in the ecosystem for which
attacks above can be performed.
Figure 1 - Network elements and vulnerable points
3 TESTING ATTACKS TO USSD AND STK DFS BASED IMPLEMENTATIONS
The following attacks and scenarios for testing the 3�1 Passive and active attacks against DFS transac‑
security of DFS transactions performed using USSD tions
and STK The goal of this test is to determine whether an
attacker can perform a passive or active attack
i. Passive and active attacks against account trans- against DFS transactions. Whereas the procedure
actions and equipment needed to perform both attacks are
ii. Testing of device authentication the same, a passive attack mainly involves an attack-
iii. Testing SIM swap attacks by IMSI verification er eavesdropping on the DFS transactions, where
iv. STK testing using SIMtrace the attacker captures, decrypts DFS messages as
v. SIM card security testing using SIM tester. they traverse the network. During an active attack,
vi. SIM clone attack the attacker directly interferes with the DFS transac-
tion, which could be in the form of a denial of service
Security testing for USSD and STK based Digital Financial Services applications 9