Page 13 - Security testing for USSD and STK based Digital Financial Services applications Security, Infrastructure and Trust Working Group
P. 13
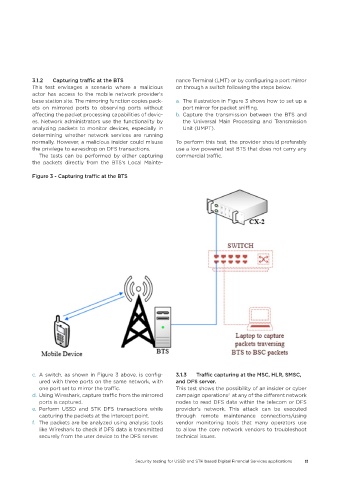
3.1.2 Capturing traffic at the BTS nance Terminal (LMT) or by configuring a port mirror
This test envisages a scenario where a malicious on through a switch following the steps below.
actor has access to the mobile network provider's
base station site. The mirroring function copies pack- a. The illustration in Figure 3 shows how to set up a
ets on mirrored ports to observing ports without port mirror for packet sniffing.
affecting the packet processing capabilities of devic- b. Capture the transmission between the BTS and
es. Network administrators use the functionality by the Universal Main Processing and Transmission
analyzing packets to monitor devices, especially in Unit (UMPT).
determining whether network services are running
normally. However, a malicious insider could misuse To perform this test, the provider should preferably
the privilege to eavesdrop on DFS transactions. use a low powered test BTS that does not carry any
The tests can be performed by either capturing commercial traffic.
the packets directly from the BTS's Local Mainte-
Figure 3 - Capturing traffic at the BTS
c. A switch, as shown in Figure 3 above, is config- 3.1.3 Traffic capturing at the MSC, HLR, SMSC,
ured with three ports on the same network, with and DFS server.
one port set to mirror the traffic. This test shows the possibility of an insider or cyber
d. Using Wireshark, capture traffic from the mirrored campaign operations at any of the different network
3
ports is captured. nodes to read DFS data within the telecom or DFS
e. Perform USSD and STK DFS transactions while provider's network. This attack can be executed
capturing the packets at the intercept point. through remote maintenance connections/using
f. The packets are be analyzed using analysis tools vendor monitoring tools that many operators use
like Wireshark to check if DFS data is transmitted to allow the core network vendors to troubleshoot
securely from the user device to the DFS server. technical issues.
Security testing for USSD and STK based Digital Financial Services applications 11