Page 52 - ITUJournal Future and evolving technologies Volume 2 (2021), Issue 1
P. 52
ITU Journal on Future and Evolving Technologies, Volume 2 (2021), Issue 1
blockchain types. We then de ine user and business pri‑ in the network. After the other nodes validate that block,
vacy within the context of PCNs and discuss possible at‑ the next block calculation starts.
tacks on the privacy of the participants. Speci ically, we Therefore, the cohort of independent participants turns
came up with novel privacy risks speci ic to PCNs. Utiliz‑ blockchain into a liberated data/asset management tech‑
ing these attack scenarios, we later survey and evaluate nology free of trusted third parties.
thoroughly the existing PCNs in terms of their privacy ca‑
pabilities based on certain metrics. This is a novel quali‑ Block-(X+1) Header Block-(X+2) Header
tative evaluation to be able to compare what each PCN is Previous Nonce Previous Nonce
Hash
Hash
offering in terms of its privacy features. Finally, we offer Block-(X) Merkle Timestamp Merkle Timestamp Block-(X+3)
potential future research issues that can be further inves‑ Root Root
tigated in the context of PCN privacy. Our work not only List of Transactions List of Transactions
is the irst to increase awareness regarding privacy issues (X+1) (X+2)
in the emerging realm of PCNs but also will help practi‑
tioners on selecting the best PCN for their needs. Fig. 1 – Blocks connected with hash.
The paper is organized as follows: Section 2 gives an
introductory background. Next, Section 3 categorizes 2.2 Cryptocurrency
the PCNs in light of common network architectures and
blockchain types. In Section 4 we de ine user and busi‑ Although it inds many areas, the most commonly used
ness privacy, discuss possible attacks on the privacy of application of blockchain technology is cryptocurrencies.
the participants in the PCNs, and present an evaluation A cryptocurrency is a cryptographically secure and veri‑
of state‑of‑the‑art solutions for what they offer in terms iable currency that can be used to purchase goods and
of privacy. Section 5 offers directions about the future re‑ services. In this paper, we will use cryptocurrency and
search on privacy in PCNs and Section 6 concludes the pa‑ money interchangeably.
per. Blockchain technology undoubtedly changed the way
data can be transferred, stored, and represented.
2. BACKGROUND Nonetheless, making a consensus on the inal state of a
distributed ledger has drawbacks. The irst drawback
2.1 Blockchain is long transaction con irmation times. For example, in
Bitcoin, a block is generated about every 10 minutes. As a
Blockchain is the underlying technology in cryptocur‑ heuristic Bitcoin users wait for 6 blocks for the inality of
rency, that brings a new distributed database which is a a transaction which yields around 60 minutes of waiting
public, transparent, persistent, and append‑only ledger time for inalizing a transaction. In Ethereum, the time
co‑hosted by the participants. With various cryptographi‑ between blocks is shorter but users wait 30 consecutive
cally veri iable methods, called Proof‑of‑X (PoX), each par‑ blocks which yield 10‑15 minutes of waiting time. Note
ticipant in the network holds the power of moderation that, as a block is limited in size, not only the throughput
of the blockchain [6]. As an example, being the irst in‑ will be limited, but also the total waiting time for the
vented and largest cryptocurrency, Bitcoin and the sec‑ users will be longer during the congested times of the
ond largest one, Ethereum, which jointly hold 75% of to‑ transfer requests. Nevertheless, if a user is in a hurry
tal market capitalization in the cryptocurrency world, uti‑ for approval of a transaction, it will need to pay larger
lize a proof‑of‑work (PoW) mechanism where a partici‑ fees to the miners than what its competitors do. This
pant has to ind a “block‑hash‑value” smaller than a jointly brings us the second drawback of using blockchain for
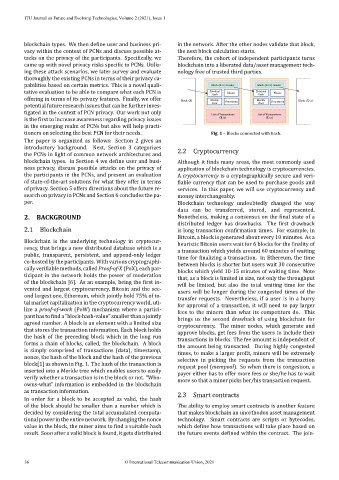
agreed number. A block is an element with a limited size cryptocurrency. The miner nodes, which generate and
that stores the transaction information. Each block holds approve blocks, get fees from the users to include their
the hash of the preceding block which in the long run transactions in blocks. The fee amount is independent of
forms a chain of blocks, called, the blockchain. A block
the amount being transacted. During highly congested
is simply comprised of transactions (data), timestamp,
times, to make a larger pro it, miners will be extremely
nonce, the hash of the block and the hash of the previous
selective in picking the requests from the transaction
block[1] as shown in Fig. 1. The hash of the transaction is request pool (mempool). So when there is congestion, a
inserted into a Merkle tree which enables users to easily payer either has to offer more fees or she/he has to wait
verify whether a transaction is in the block or not. “Who‑ more so that a miner picks her/his transaction request.
owns‑what” information is embedded in the blockchain
as transaction information.
2.3 Smart contracts
In order for a block to be accepted as valid, the hash
of the block should be smaller than a number which is The ability to employ smart contracts is another feature
decided by considering the total accumulated computa‑ that makes blockchain an unorthodox asset management
tional powerin theentire network. Bychanging the nonce technology. Smart contracts are scripts or bytecodes,
value in the block, the miner aims to ind a suitable hash which de ine how transactions will take place based on
result. Soon after a valid block is found, it gets distributed the future events de ined within the contract. The join‑
36 © International Telecommunication Union, 2021